We’ve all been there: your computer isn’t working, and you don’t know what to do. Some of us are more reluctant to ask for help than others, but at some point, we give in and call Tech Support.
We trust that Tech Support will save us: they have all the answers, and we are helpless troglodytes by comparison. Sadly, this kind of blind trust is the perfect tool for con artists, and they have been taking advantage of it so often that it now has a name: Tech Support Fraud.
In this month’s Cybercrime Blog Series, we will give you an overview of how this fraud is perpetrated, and how to protect yourself and your business.
What is Tech Support Fraud?
Tech support fraud began to be reported around 2008 to tech companies whose customers had been victimized. In 2014, Microsoft filed suit against several companies based in India for impersonating their reps to obtain control of their customer’s computers and defraud them. At that time, almost 6 years ago, Microsoft stated that 3.3 million Americans fall victim to Tech Support Fraud every year and had collectively lost $1.5 billion. Recent data from Microsoft, as indicated in the graph below, shows that this issue has not improved, with their reported cases averaging over 12,000 a month in 2017 alone.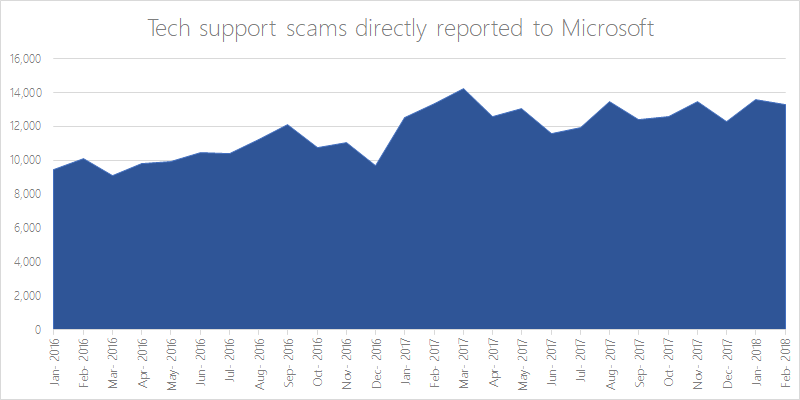
Source: Microsoft Defender ATP Research Team
Not every Tech Support Fraud scheme is identical, but they usually involve impersonating a representative from a legitimate company such as Microsoft or Apple.
Fraudsters must first find a victim, which is done in a variety of ways:
- Unsolicited phone calls: someone claiming to be from Tech Support for a legitimate company informs you of a made-up problem and offers to fix it
- A pop-up message: appearing to be from a legitimate company, these pop ups often freeze the user’s computer, and advise them to call a tech support number provided
- Search Engine Optimization: paying to have an illegitimate website appear at the top of search; at a glance it seems to be the legitimate domain of a legitimate company
- URL hijacking: taking advantage of common typos people make when typing in a website address, and building a fake website that appears legitimate
Once they make verbal contact with the victim, they convince the victim to allow them access to their device by downloading remote access software. This enables the fraudster to read computer files with personal and financial information such as usernames, passwords, bank accounts, social insurance numbers, healthcare information, credit cards, etc. In addition, the fraudster will often install spyware on the victim’s computer.
They may attempt to convince the victim that their computer has been infected with a virus and sell them worthless software to fix it or encourage them to enroll in a phony maintenance or warranty program. They may also convince victims that their license for their operating system or other programs has expired and they must pay to renew them. For payment, the fraudster will direct the victim to a website that requires them to enter their credit card details and other personal information.
Some are even more aggressive, taking over the victims computer and/or bank account and demanding a ransom before they will relinquish control (a much more hands-on variation on the cybercrime we profiled last month: Ransomware). Paying the requested funds will not always end the harassment, with fraudsters continuing to mislead and demand more money.
How to Protect Yourself
Tech Support Scams usually target individuals and small businesses located in the USA and Canada. Victims of these scams are often from vulnerable groups such as the elderly, or individuals with low computer literacy or “tech IQs”.
To be clear, this is not a matter of intellect: computer literacy refers to one’s familiarity with computers, the internet, or technology. Without sufficient computer literacy, it’s difficult for victims to identify people who are behaving in abnormally or making false claims. Even those who do have relatively high computer literacy levels can still fall victim to these fraudsters, as they continue to be more and more sophisticated in their methods and prey on the perceived authority of “tech support” agents.
There are a variety of strategies to protect yourself against this kind of fraud:
1) Protect your Devices
Industry-standard, frequently updated anti-virus software is vital to protecting yourself. These tools go beyond basic protections built into operating systems and are constantly updated to keep up with the newest viruses and scams.
2) Check their Homework
The internet is a useful tool if you’re suspicious of an interaction or message. Use it to double check phone numbers and URLs, Google the issue to see if anyone else has posted information about it, read sites that are not listed in the “promoted” area of Google, and don’t be afraid to question what you’re being told.
If there is a widespread issue, press releases or help articles will be posted to official company websites to inform customers and help them resolve it.
3) Train your Staff
Train your staff on common scams like this one and tell them how to protect themselves. There are helpful resources available from trusted sources, such as this Consumer Information Report from the US Federal Trade Commission. Training should occur at regular intervals and be updated with new information. “One-and-done” training isn’t effective when these schemes are evolving constantly.
4) Raise your Staff's Computer Literacy
Computer literacy is no longer optional in a modern workplace. We don’t all need to be programmers, but we should be familiar with our own business tools.
Empower your staff by providing them with resources to increase their tech IQ and establish familiarity with your systems. This will allow them to be able to spot unusual activity more confidently and limit their ability to be manipulated.
5) Establish IT Procedures
Even small businesses with just a handful of employees should establish basic guidelines for handling tech-related issues. Perhaps you may want to contract a trusted third-party IT company that can serve as a safety net for any issues beyond the power of Google. Perhaps it’s as simple as assigning a person on your team “in charge” of handling all systems-related issues such as contacting software providers with problems or renewing licenses.
In short, don’t expect your staff to know what to do in the moment if you haven’t taken the time to tell them.
6) Use Common-Sense
Whether via email, phone, or pop-up, companies such as Microsoft will never initiate first-contact with you to provide tech support, and they will never “lock you out” of your own computer. If we employ common-sense, we can understand why.
Companies do not have the resources to contact millions of users to proactively offer technical support that hasn’t been requested. Furthermore, these companies would be in a legal and PR nightmare if they were to remotely disable people’s computers, which are private property, simple to extort money from them.
7) Does it "feel" right?
Companies like Apple or Microsoft have very defined branding and style which they employ in every way that they interact with their customers. They use recognizable symbols and color-schemes, they repeat themes, and they even use a certain “voice” to speak to customers. This is their brand identity, and it is harder to copy than scammers think. At first it may be hard to put your finger on why, but they may not “feel” right.
Is the logo old? This would be highly unlikely from a major tech company.
Are there obvious and frequent spelling or grammar errors? Again, these types of errors are unlikely to have made it through the chain of command at a tech giant like Apple.
Trusting your gut is sometimes the best way to protect yourself, and these tiny errors can set off alarm bells even if you’re not sure why.
8) Don't Respond to High-Pressure Tactics
When speaking with customers, calls from companies such as Microsoft are monitored and recorded at all times. Agents also receive extensive customer service training and may even be working from a script.
Fraudsters, however, will continue to put more and more pressure on you as you exhibit more resistance to what they say. They will threaten you, instill fear in you, and may even become verbally abusive. This is a dead giveaway – any legitimate tech support agent would be risking immediate termination for that kind of behaviour. Large, legitimate companies discourage this kind of behaviour at all costs. Even if a customer is being abusive towards them, legitimate reps are trained to keep their cool and always be polite.
Responding to an Attack
If you become aware that a Tech Support Fraud has been perpetrated against you or your company, or is currently in progress, here are the immediate steps you need to take:
1) Sever the Connection
You may realize something is fishy while still on the phone with your hacker, or while a remote connection has already been activated. If you believe your device is compromised, the best possible action is to immediately sever that connection.
These hackers need to maintain a connection to your PC, and that connection requires two things: the internet and electricity.
- Desktop PCs must be plugged in to remain “on” – when in doubt, literally unplug your computer from the wall.
- You can force an immediate shut down by holding down the power button for 5-10 seconds– this is the only way to immediately shut down a laptop (which has a battery).
- If possible, switch off your WiFi receiver and/or unplug any ethernet cables. Severing a connection to the internet will disconnect any remote control of your PC.
If you can’t figure out how to disconnect your WiFi signal, unplug your router.
2) Report It
Notify law enforcement and your financial institutions immediately. They can place temporary locks on accounts or add more layers of security to prevent a breach in the immediate aftermath of an attempt to steal your data. This flag on your file will also raise suspicions both digitally and in person if someone attempts to steal your identity using the information they obtained.
3) Immediately Change All Passwords
This includes those to your online banking or any websites which are connected to your email address(es).
Hackers know that people tend to re-use passwords. For example, you might use the same password for LinkedIn that you do for your email. Maybe they can’t get into your online banking account using your LinkedIn password, but if that password is the same as your Gmail account, knowing the password would give them access to your inbox.
Simply clicking “forgot password” makes it easy to completely hijack any accounts linked to that email, resetting passwords so you can’t get back in and (perhaps most dangerous) allow them to impersonate you and drain your accounts without your bank or other financial institution realizing anything is amiss until it’s too late.
Don’t forget to do this from an uncompromised device. If the hacker was able to install key logging software onto the affected computer, using it to change passwords after the attack will deliver the new passwords right into their lap, and speed up their work significantly.
Click here to read other articles in our Cybercrime Series.
If you'd like to receive our blog posts directly to your inbox, or get other news and updates from AscendantFX, subscribe to our mailing list!
 About the Author: Bernard's role as EVP, Chief Compliance Officer for AscendantFX, and previously as a Commander in the Royal Canadian Mounted Police (RCMP) investigating organized crime, allows him to be uniquely qualified to give insight into the dangers which these many different frauds, scams, and hacks present to businesses and individuals.
About the Author: Bernard's role as EVP, Chief Compliance Officer for AscendantFX, and previously as a Commander in the Royal Canadian Mounted Police (RCMP) investigating organized crime, allows him to be uniquely qualified to give insight into the dangers which these many different frauds, scams, and hacks present to businesses and individuals.










